Improve your Network observability with DPI on Ultraconnect SD-WAN

The emergence of the cloud has been one of the most significant changes in business operations in recent years. Enterprises have gained agility and flexibility that dramatically increases their productivity and efficiency by utilizing servers elsewhere worldwide over the Internet for computational, storage, and network functions instead of maintaining this Infrastructure locally. Recently, this Infrastructure as a Service (IaaS) methodology has been expanded to include the operation of corporate infrastructures through a multi-cloud architecture instead of a single cloud.
The use of Ultraconnect SD-WAN to address network and security issues
1. Control firewalls and routers in traditional networks
With orchestration, you can provision more quickly while making faults and help desks simpler.
2. A lot of availability SD-Internet
Our packet-based technology joins together internet connections to increase bandwidth while preventing downtime. Perfect for applications that require high-quality internet, SIP voice, video, and other services.
3. Software for SD-WAN 2.0
Affordable hardware Virtualized or containerized X86 Link aggregation and load balancing based on packets increases the amount of available bandwidth. The same IP failover prevents call drops.
What does DPI mean for your business?
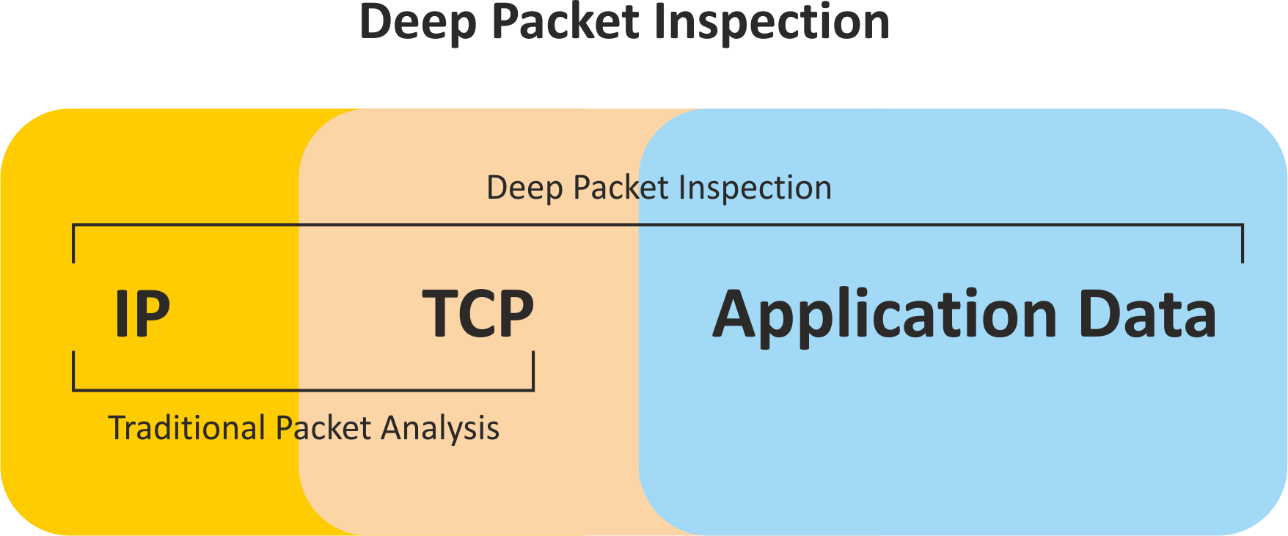
Deep packet inspection (DPI) & Traditional Packet Inspection
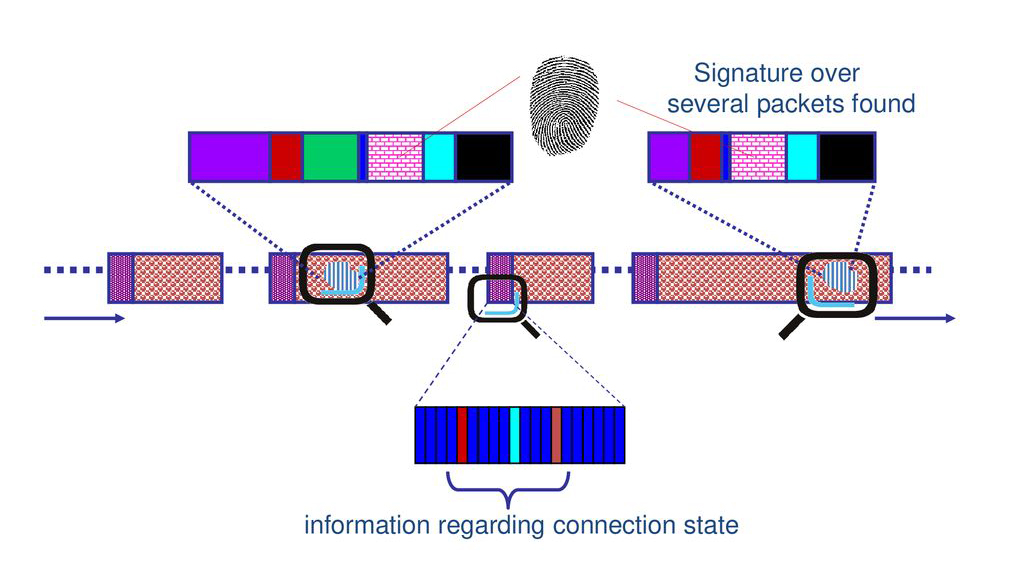
Deep packet inspection (DPI) is a sophisticated technique for monitoring and controlling network traffic. It is a type of packet filtering that finds, recognizes, categorizes, and redirects or blocks packets of data with data or code payloads that traditional packet screening.
To connect users to an organization's workloads, applications, and services Infrastructure, Ultraconnect SD-WAN can be implemented using physical or virtual appliances that are hosted on-premises or in the cloud. SD-WAN Ultra connect abstracts network components to improve network communications.
To further protect Ultraconnect SD-WANS, DPI is added. Even though the Ultraconnect SD-WAN has a secure overlay, many businesses connect their branch locations immediately to the Internet, putting them at risk of additional security threats. To stop attempts on any branch from spreading throughout the entire business, DPI offers complete application control and visibility to segment branch offices from the WAN.
A more reliable method for implementing network packet filtering is made possible by the deep packet inspection's wealthy data evaluation, which enables DPI to recognize and stop a variety of complex threats that are concealed in network data streams, such as: more effectively
1. Malware
2. Attempts at data exfiltration
3. Content regulations broken
4. Communications used in criminal control and command
Developing deep packet inspection capabilities has overcome the limitations of conventional firewalls that rely on stateful packet inspection. Consider airport security to comprehend better the advancement that deep packet inspection offers.
Deep packet inspection: how does it operate?
Deep packet inspection looks at the information contained in packets as they pass through a specific checkpoint and, using rules set by an organization, an internet service provider, or a network manager, makes real-time decisions based on that information.
Earlier packet filtering techniques only examined packet header data, comparable to reading an address on an envelope without knowing what's inside.
Firewalls only had the processing power they needed recently to conduct in-depth inspections on large amounts of traffic in real time. Because of technological advances, DPI can now perform more detailed reviews and examine packet headers and data.
How to get started with DPI?
There are several methods to successfully implement a Deep Packet Inspection-based security control in a public cloud environment.
The first is to make use of the vendor solutions that were created specifically for this situation. These could be virtual instances with built-in IDS and Application Layer 7 controls. (for which DPI is required). The simplicity of management, support, and deployment is beneficial.
Lastly, a virtual network TAP, such as the one provided by Microsoft Azure, can deliver a complete network traffic feed to any location. A malware sandbox, a NetFlow sensor, or an intrusion detection system could be used. Even though the destination system is not inline, this option's wide range of flexibility enables inter-device messaging, for example, where an IDS automatically instructs a firewall to block a malicious IP that an IDS signature has identified.
Choose the ''Enable Deep Packet Inspection'' check box in the Configuration Editor's Global > Applications > DPI Settings section to enable DPI library classification.
Techniques for Deep packet inspection
Matching patterns or signatures
A firewall examines each packet with IDS capabilities toward a database containing known network attacks. It searches for patterns proven to be malicious and, if it discovers one, blocks the traffic. This method's drawback is that it relies on frequently revised signatures to function effectively, and this approach is only effective against recognized hazards or assaults. Daily threat discoveries necessitate ongoing signature updates, essential for the firewall to identify new threats and keep the network safe.
Protocol irregularity
Because it does not simply allow all content that does not match the signature database, the protocol anomaly method—again, used by firewalls with an IDS—does not have the built-in vulnerability of the pattern/signature matching method. Instead, it adopts a default deny strategy. The firewall decides which content and traffic should be allowed based on protocol definitions. As a result, similar to signature matching, this technique safeguards the network from unidentified threats.
System for preventing intrusion (IPS)
IPS solutions can stop unwanted packets from arriving based on their contents, allowing them to block identified attacks in real-time. Thus, the IPS will actively reject network traffic following a defined rule set if a specific packet represents an established security threat. One disadvantage of IPS is the requirement to routinely update the cyber threat database with details about new dangers, and the risk of false positives is also high.
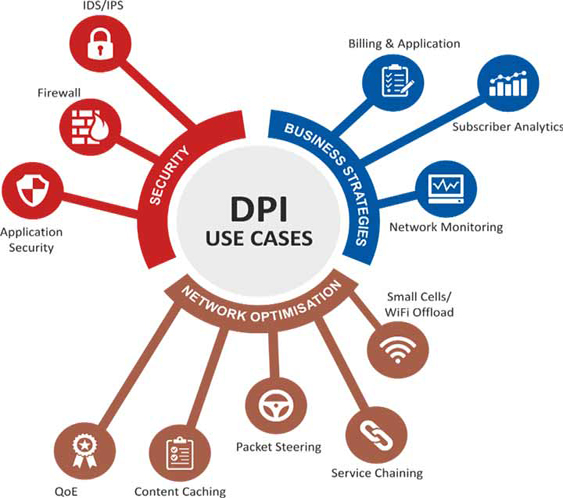
Deep packet inspection applications
A variety of new and enhanced security use cases are made possible by analyzing traffic patterns through deep packet inspection.
Removing malware
Deep packet inspection can be used with threat detection algorithms to stop malware before it harms endpoints and other network assets. As a result, it can aid in filtering out ransomware, virus, spyware, and worm activity. Additionally, it offers network visibility that can be used to identify unusual traffic patterns and notify security teams of malicious activity suggestive of active compromises. Heuristic analysis can be applied to this visibility to identify more comprehensive ranges of threats.
Putting a stop to data leaks
Deep inspection of packets can be used for both outgoing and incoming network activity. This means that organizations can use this analysis to set filters to thwart data theft attempts by outside attackers or potential data escapes brought on by both negligent and malicious insiders.
Enforcement of content policies
Organizations can block or restrict access to hazardous or unauthorized applications, like peer-to-peer downloaders, thanks to the increased application visibility provided by deep packet inspection. Similarly, DPI's deeper analysis paves the way for enterprises to block policy-violating usage trends or stop unapproved access to the information within corporate-approved applications.
Advantages and drawbacks of DPI
Network response times, latency in network applications, and other things can all be measured and monitored with deep packet inspection software. It assists in calculating the time required for a packet to travel from its source to its destination. Administrators can use this data to identify the leading causes of problems, the affected applications, the number of traffic measures, and more. Evaluating many applications and how quickly they respond to the implementation of deep packet inspection is simpler. It can track various metrics and direct your attention to the applications' meta values. Using deep packet inspection software, users or IT departments can detect, filter, and eliminate non-business traffic.
The difficulty of encrypted traffic is another issue. Although some firewalls claim to perform deep packet inspection on HTTPS traffic, many hardware-based security devices need help handling the processor-intensive task of decrypting data and inspecting it while traffic is flowing. In response, administrators frequently decide to disable the feature in their firewalls.
Takeaway
Both the SD-WAN market and the competition are expanding quickly. With the help of Ultraconnect SD-WAN, you can aid in expanding your network past your physical boundaries. You can choose with ease thanks to SD-WAN aggregators. Connect your local loops to the closest aggregator, and from there, you can quickly and easily add a site to your SD-WAN. Vendors of SD-WAN require DPI to support essential functions like real-time application visibility, improved security features, and analytics. This also addresses the use cases of commercial clients.
Businesses can also use publicly accessible aggregators or set up on their own. You have the option of using them privately or making them public and using a federated model to sell accessibility to other providers.
One example is the visualization and reporting of application security and performance diagnostics at important customer sites and cloud data centers. SD-WAN vendors can now offer intelligent routing, traffic steering, and enterprise application efficiency with advanced reporting capabilities thanks to DPI technology. Cost and performance advantages, however, are only helpful with solid end-to-end security.